SSL and HTTPS: Part II
a comprehensive (sort of) beginners guide
February 15, 2016
Setting Up Secure
We'll continue with the example presented in the previous post about our dentist. Because we are going to transmit sensitive information on our website, we decided to encrypt the data it sends by using HTTPS.
Setting this up is surprisingly easy. Unfortunately, it is webserver
specific and out of scope for this post.
But basically, you just need to set
some flags in your Apache/Nginx/etc config files.
You'd need to look up the specifics, but essentially you just set
secure = true.
With that, you are halfway there. Now you just need an SSL Certificate, and to tell your webserver where that certificate lives.
What is SSL?
There are a number of places you can buy an SSL certificate. For no good reason, I like namecheap.
There are two main criteria when looking at SSL Certs. 1. What is the level of trust that I need. and 2. How many domains do I need covered?
Trust
If you are a global bank, you need a lot of trust. For a customer to give you a significant amount of money, they need to know that you are who you say you are and that you are keeping their dollars and information safe. If you are a dentist, it's fair the say the level of trust needed is less.
Because of that, you can buy a really expensive SSL cert that says to the world, "You can trust everything about this website." This cert costs a lot of money, because the certificate authorizer calls the company and talks to people, does independent research, etc., to make sure this company is who they claim. I don't know any of the specifics, but there is a complex vetting process that allows a certificate to be issued that conveys "super high level of trust here".
The level of certification is available for review in the address bar. This is what it looks like when I log into my bank account—

That big green box lets everyone know, PNC paid a lot of money to be properly vetted. They are who they say they are and they encrypt their data. You can trust them.
Digging down a little deeper, let's look at The New York Times. When I browse articles on their website, there is no need to encrypt the information. They can send articles as plain-text back and forth. This is what the url bar looks like—
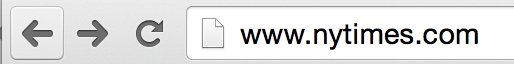
But when I log in to my account at The New York Times, things change. In this section of the website, they keep addresses and take credit card information. Here is the url bar—
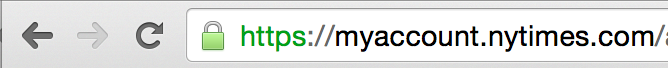
Domains
This section is the less interesting of the two. The more subdomains your website has, the more expensive your SSL cert. That is, as dentist you may only have 'greatdentist.com'. But some people have 'https://foo.mywebsite.com' and 'https://bar.mywebsite.com'. The more subdomains you have, the price goes up. You can buy a wildcard cert, that covers everything. 'https://*.mywebsite.com'.
More with SSL
A basic SSL cert is ~$10. A wildcard cert is ~$100. And a top-of-the-line enterprise cert is ~$1,000.
You bought my certificate... but now what? Well, follow the instructions. The implementation details are outside the scope of this discussion. Trust be told, this is the part that took me longer than it should have. But basically, you need to 'activate' the cert by filling out some questions about your website and company and the issuer will send it to you via email. Then you need to transform the file sent to you to a CSR, which is just another file type. (There are lots of good resources with instructions .) Then copy that file onto your server, and update the webserver config files to let it know where it is saved.
The file itself looks like a bunch of letters and numbers, but everything you've been approved for is hidden in that text. And whenever someone goes to that url address the level of trust is known and displayed.
This Raises Some Questions
Q: Why isn't every website secure?
A: They should be. And they probably will be soon. But right now, you can't force everyone to buy an SSL cert. More on this in a minute.
Q: Why do SSL certs cost money?
A: The company that issues the certs needs to make money. These companies know how to vet applications, but have obvious costs.
Q: Can I make my site secure without an SSL cert?
A: Yes. These things are not intrinsically coupled. There is nothing that stops
you from changing the settings on your webserver config to secure = true
and not buying an SSL.
However, when the web browser sees there is no valid SSL it issues a
BIG warning to the user.
So while technically this can be done (encryption without SSL),
it is not practical for any consumer-facing website.
The Future
It only makes sense for all sites to be secure. I press you to think of a usecase where plain text is preferable. It's not much extra work, and better to be safe than sorry.
For this reason, Mozilla recently announced they are phasing out HTTP in Firefox. It is already deprecated. Google has similar plans with Chrome.
To make this a reality, it is now possible to get free SSL Certificates. Let's Encrypt is a public benefit corporation (backed by big tech sponsors) that grant certs for $0. They do not issue fancy certs and it looks like they are quicker to expire, but it is illustrative of the directions thing are moving. Because without free SSL certificates, it is not reasonably possible to require all sites to use HTTPS.
Wrapping Up
I hope some aspects of HTTPS and SSL are clearer than they were before. I'm not an expert, I just changed two SSL certs that lapsed. If I've got something wrong, please let me know!
Have anything to say? Questions or feedback? Tweet at me @cmmn_nighthawk!